By Dell Cameron, Gizmodo.
June 27, 2020
https://popularresistance.org/dojs-new-wikileaks-indictment-has-significant-convenient-plot-holes/
In its push to extradite WikiLeaks founder Julian Assange from the U.K., the U.S. Justice Department on Wednesday published a superseding indictment aimed at broadening “the scope of the conspiracy surrounding alleged computer intrusions with which Assange was previously charged.” The names of certain organizations and individuals are masked, including that of a paid FBI informant who stole money from WikiLeaks and later confessed to having sex with nine underage boys in exchange for money and other valuables.
A decent chunk of the filing relates to Chelsea Manning, her interactions with Assange and other possible ties to known WikiLeaks associates, which serve as the foundation for the bulk of the charges against Assange, including multiple counts of espionage.
But in hopes of linking Assange to other “unlawful overt acts” as part of a broader conspiracy—one goal of which is connecting Assange to crimes against a NATO ally of the country considering his extradition—DOJ describes several alleged interactions between Assange and Anonymous hackers involved in major criminal operations. Considerable context is omitted from the descriptions of these events, however, including the FBI’s own role in furthering attacks by Anonymous against American businesses and foreign governments in South America and the Middle East, based on a review of sealed evidence by Gizmodo.
A section of the indictment titled “Sabu, Hammond, and ASSANGE” begins on the date December 25, 2011, and refers to an attack on servers belonging to a private firm identified only as “Intelligence Consulting Company.” This is obviously Stratfor, the Austin-based private intelligence company whose millions of pilfered emails comprise the WikiLeaks drop known as theGlobal Intelligence Files.
DOJ omits several crucial details about the Stratfor hack in its attempts to name Assange as a conspirator in a breach that happened without his knowledge. Most notably, prosecutors exclude that the actual breach of Stratfor’s security, in late 2011, occurred 83 days prior to the events they describe, unknownst by anyone DOJ identifies as part of the conspiracy, including Assange.
This has gone mostly unreported due to the fact that all of the evidence related to the hack was sealed by a federal judge in Manhattan. Attempts by the New York Times and other outlets to acquire the evidence in court all failed. Nevertheless, nearly all of it was leaked to a handful of reporters in 2013 and today form the basis of multiple detailed accounts of the hack and surrounding events. (A portion of the material has been publicly accessible for years.)
One key document is a confidential computer forensics report, completed in February 2012, describing the Stratfor breach. The report was completed by investigators working for Verizon, which Stratfor contracted about five days after the public became aware of the breach. It lays out several important facts: The first is that attempts to breach Stratfor’s email server began on September 29, 2011, and that four days later, a brute force attack against a specific user account was successful.
This break-in detailed in the confidential report occurred two months before anyone prosecutors have blamed for the attack even knew of the company’s existence.
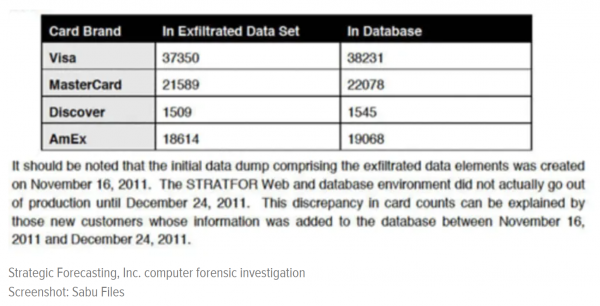
On November 16, the data dump containing the credit card information of Stratfor customers was created. Notably, this predates the DOJ’s own timeline of Anonymous’ involvement by 19 days. That this is the actual credit card file ultimately leaked by Anonymous is indisputable: The dataset contains 79,062 credit cards, the exact number of cards held by Stratfor on November 16, according to the forensics report. By the time Anonymous published its list, Stratfor’s database contained an additional 1,860 cards, none of which were included in the leak.
The first Anonymous figure identified by DOJ as part of the Stratfor hack doesn’t become aware of the breach until early December, according to DOJ’s own timeline of events. In 2012, the FBI fed news reporters, including those at the New York Times, false information about how this all transpired. The FBI claimed that an Anonymous hacker found a way into Stratfor’s network on December 6 and then notified a member of his team—who happened to be an FBI informant.
In reality, the exact opposite happened.
Prosecutors have never mentioned, nor has the FBI ever acknowledged the capture of, the hacker actually responsible for breaching Stratfor and creating the stolen credit card file. The narrative has always been that Jeremy Hammond, a hacker affiliated with the Anonymous-offshoot Antisec, was chiefly responsible for the breach. (Hammond is currently serving the final year of his 10-year sentence for hacking Stratfor.)
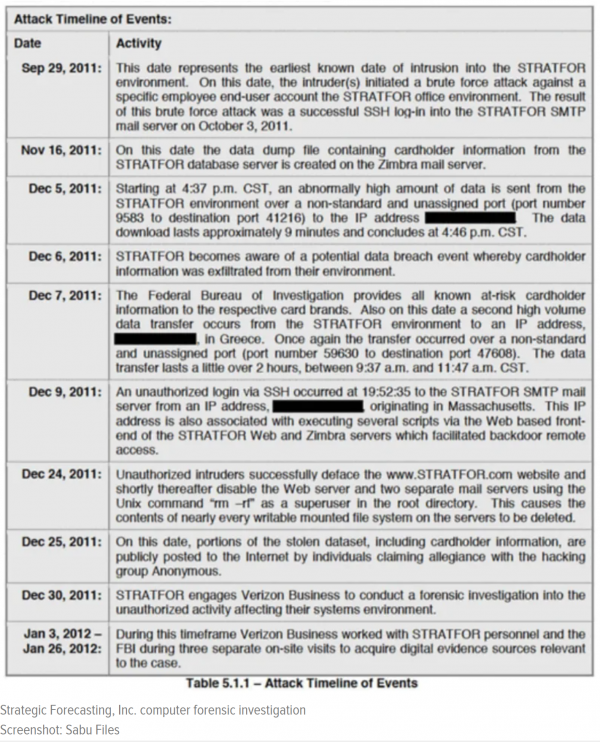
For certain, Hammond gleefully ransacked Stratfor, defaced its website, encouraged others to commit fraud using its stolen credit cards, and on December 24, 2011, inputted the commands that disabled its web server and deleted its file systems. But prior to December 4, the date an FBI informant (“Sabu”) offered him the means to access those systems, Hammond had no apparent knowledge of the company’s existence.
Evidence collected by the FBI, which DOJ has fought to keep concealed, shows the hacker responsible for breaching Stratfor (known only as “Hyrriiya”) was closely tied with a group of hackers whose central focus was infiltrating the Syrian government—the same group behind the leak of the Syria Files, more than 2 million emails from Syrian government officials published by WikiLeaks in July 2012.
Moreover, the evidence appears to show a clear violation of DOJ’s guidelines for the use of confidential informants, which expressly forbid informants from initiating or instigating “a plan or strategy to commit a federal, state, or local offense.” Despite claiming in court that its informant was under constant surveillance and worked side-by-side with agents throughout his cooperation, an FBI official later said of any alleged unlawful conduct: “It’s not like we watched him every time he got up to get a coke.” (This also appears untrue as prosecutors claimed in 2014 there was a webcam in his apartment.)
In one of the most egregious examples of this violation, records show the informant providing Hammond complete credit card data belonging to a member of the International Association of Chiefs of Police and an employee of Raytheon as evidence the breach is authentic. Hammond responds that he’s interested and wants to “sink [his] teeth” into the target.
At the time Stratfor was hacked, companies rarely faced any scrutiny for suffering data breaches. Were the same hack to occur today, coverage of the event would likely be different. After Equifax announced its breach in 2017, the company was investigated federally and excoriated publicly, its reputation essentially torched. Stratfor, meanwhile, quietly paid out a meager $1.7 million settlement and was largely portrayed as a victim in the press.
In truth, Stratfor set the stage for its own devastating breach through its own sheer negligence. Its security, or lack thereof, was appalling, according to its own forensic report. The company had virtually no controls over remote access to its network, which was not protected by a firewall and lacked proper file integrity-monitoring. It had no password management policy. According to the report, staff “commonly use the same password to access email as the password to remotely access a system containing sensitive information.”
In 2011, Stratfor was, the report found, ignoring all routine data security standards established by the payment card industry: no firewall, no encryption, no regularly updated anti-virus software, no need-to-know restricted access, no network monitoring, no regular audits of its systems, and no existing policy to address information security. The server that held Stratfor’s unsecured credit card data wasn’t even segregating from its email server, which was the hackers’ point of entry and the only reason any financial information was stolen in the first place.
If the same hack were to have happened this year, the company would wind up eating the lion’s share of the blame.
Perhaps the most absurd twist is that Dallas-based journalist Barrett Brown ended up getting slapped with nearly $900,000 in restitution to Stratfor, even though Brown had no advanced knowledge of the attack and, to be blunt, couldn’t hack his way out of a paper bag.
As with Hammond, Brown took a deal in an effort to avoid potentially decades in prison. But in trying to ensure Brown got the harshest sentence possible, federal prosecutors repeatedly painted him as being closely allied with the hackers behind the Stratfor breach. This despite the fact that DOJ quietly withheld evidence obtained by an informant obliterating that theory. This evidence showed that the hackers secretly loathed Brown and had even discussed implicating him in the crime—textbook Brady material, which would have all but upended the government’s account of Brown being integral to the breach.
As Gizmodo previously reported, there is likely ample evidence to show that WikiLeaks aided the Stratfor hackers in the wake of the attack, after the fact. But in several places, Gizmodo can confirm, the indictment attributes statements directly to Assange when, in reality, those conversations were relayed second-hand. (Assange is also known for using a variety of methods to obscure his identity online including, notoriously, referring to himself in the third-person.) At best, these are copies of exchanges taken from chat rooms in which a user claims to be Assange, which is not likely to hold up in court.
The evidence does show that someone alleging to be Assange provided the Stratfor hackers with a script designed to help them more easily navigate the more than 5 million emails they stole (though, as FBI’s own evidence shows, the hackers found the tool was practically useless.) Nevertheless, like Brown, the evidence also shows Assange had no foreknowledge of the attack. Without WikiLeaks’ involvement, Stratfor’s customers would have still suffered the same amount of financial harm, the company’s systems would have still been destroyed, and its emails would have ended up splattered across the internet anyway, in one form or another.
Regardless of whatever alleged crimes Assange may actually be guilty of—if any—that shouldn’t distract from the fact that DOJ’s timeline of events is woefully misleading. The agency’s handling of the Stratfor breach should not be cast as a model for how to prosecute computer crimes. It is at best a paradigm for evidence mismanagement, and at worst, a glaring case of deliberate prosecutorial misconduct.
No comments:
Post a Comment